I’m using Signal, but after I found out that it’s not as privacy-friendly as it claims, I’m uneasy about sharing my address there. I trust the person who asked for my address, but not the service. What’s a safe way to share? I was thinking of something like a self-destructing pastebin, but surely you have better ideas.
Which of Signals privacy claims are false?
Pretty much everything about it is unverifiable, because its a centralized service and you ultimately don’t know what the server is running. Contrast that with self-hostable apps which must pass verifiability checks, because people can host their own instance.
Clients are open source. Independent clients exists and they work. So the server must kind of do what signal claims, otherwise those devs would notice.
You have no idea what the server is running. It has your phone number, ie your real name and address, and it knows who you sent messages to.
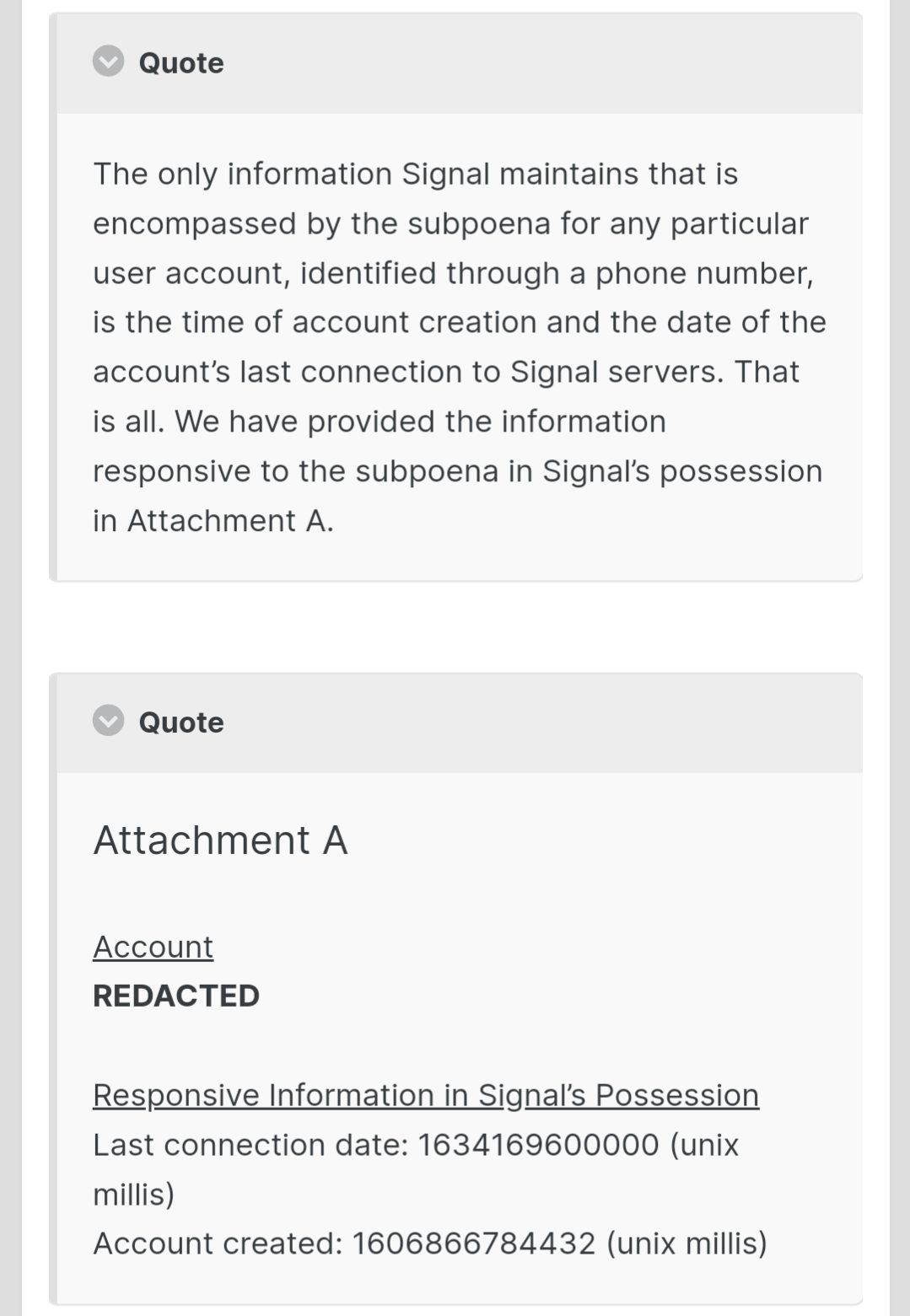
But it doesn’t though. That information has been subpoenaed from signal in the past. They don’t have access to it to give. This is public information.
As comment in thread points out, the subpoenaed info was essentially useless.
Yeah that’s exactly my point. Other guys was listing all these things the signal has stored but they really just don’t want access to any of it.
IDK if this an issue on my app specifically, but it looks like you put the wrong things in the parentheses there.
Turn on Sealed Sender
This is suspicion on the level of “you can’t be sure reality didn’t just pop into existence 10 seconds ago”. You can never be 100% sure of what others are doing on their hardware, or of anything really, especially if other people are involved. Your chat partners could leak all your chats and metadata for all you know!
What we do know is that Signal is operated by a non-profit foundation, their client and protocol are open source and considered the gold standard for privacy by pretty much every expert on the subject, they had multiple independent audits and a very good track record, they were subpoenaed and couldn’t comply because they didn’t have the requested data. That’s about as good as you can get.
deleted by creator
Better use a cipher then for your pen and paper transmission. Invisible ink as well.
Matrix and even Signal you reject for some reason work fine with no one being able to see the content of your message except the one you sent it to.
I’ve never heard anyone other than OP have any privacy concerns over Signal. Their encryption method is rock-solid, and they win the award for best response to a government subpoena
I have been using bw for years and never occurred to me to click on send. I thought it was for sharing passwords or something.
I mean it can be. You can put anything you want there and send it on it’s way
Signal is trustworthy
I guess you can use wormhole to transport the data to your peer, and if you’re extra paranoid encrypt it asymmetrically with something like age.
Then again you can just encrypt it with age and send it over Signal. There should be no risk involved in sharing public keys even if you don’t trust their servers.
Unrelated but how did a ~1 year old post get in my hot frontpage
A Lemmy bug that surfaces old posts on “Hot” coupled with a bunch of recent comments actually making it hot.
That makes me think it’s simply not using the post’s timestamp like it is supposed to, so it is working like Active or New Comments.
Use briar.
When I need extreme security and privacy, I use qTox
https://1ty.me would be described as a “self-destruting pastebin.” I’d generally be careful about what you can put in there (e.g. put partial information in it with no context) but it seems to do the job.
But the real answer is probably PGP/GPG.
Here is a good resource for these kinds of questions: https://www.privacyguides.org/en/tools/
You can both get PGP, exchange public keys and send encrypted text with whatever service you want.
XMPP / Jabber with OMEMO encryption. Lots of free servers and clients.
The cloud is just someone else’s computer. If you want real privacy self host it. Raspberry Pi are cheap again.












